If your New Year’s resolution is to *finally* fix up your website, we’ve got you covered with five ideas that will improve your site’s performance and your bottom line
- Check your site speed. We like the free GT Metrix tool. If your website is getting a C, D, or worse, it’s time to invest in some performance enhancements. Site speed is important for both SEO (search engine optimization), and user experience. Common culprits of a slow site?
- Bad hosting
- Too many large, uncompressed images
- No caching
- Not using a CDN (content delivery network)
- Too many plugins or a heavy commercial theme
Some of these are fast and easy to fix, and others will require a little more time, but the dividends will be worth the investment
2. Take a gander at your Google Analytics reports. Don’t have Google Analytics installed on your site? Install it. You’ll get good, actionable data that will help you make informed decisions about your site. A few reports we like include:
- Audience > Mobile
- Acquisition > Overview
- Behavior > Site Content > All Pages
- Conversions > Goals > Source / Medium
Pro tip: If you don’t have Conversion Goals set up, do it. Just do it.
3. Conduct a competitive audit. Been a while since you’ve checked out the competitors’ websites? Spend some time evaluating their designs, new features and functionality, and content.
- Do their sites look newer and more attractive than yours?
- How do their websites look on a mobile device compared to yours?
- Have they added special functionality to help visitors have a better, more productive experience?
- Have they gotten beautiful new photography; shot some videos; or invested in a relevant blog, podcast, or whitepaper?
Your competitors’ websites are just a click away for customers, so it’s wise to keep abreast of what the competition is doing—or better yet, beat them to the punch.
Extra credit: spend some time thoughtfully browsing other websites outside your market or industry. Pay attention to special design elements, features, and functionality, and consider how your website could benefit from a similar approach.
4. Invest in new photos. Great photography can make all the difference in a website, and can be a simple way to take a site from “good” to “great.” If you’ve been using the same old photos for years, or are relying on stock photography, consider a photo shoot to freshen up the website. As an added bonus, you’ll be developing a library that you can rely on for your other marketing materials, social presence, and more, too. Consider:
- If you have an e-commerce website, aim to include 5-7 photos per product
- Meet the team: a group photo and individual headshots (plus some “just for fun” photos!)
- Photos that showcase your office or facility
5. Switch to an easy-to-use content management system. If you’re still using an old hard-coded website, or you’re using a CMS (content management system) that’s hard to manage, consider upgrading to a platform like WordPress. You’ll find that the website is easier to update, which means you’re more likely to keep it up-to-date with fresh content, which the search engines and real visitors will appreciate. You’ll also find that it’s easier to add new features and functionality—in the form of plugins—than may have been possible before.
Want help with any (or all) of the above? Schedule a call and let’s discuss how we can make your website New Year’s Resolutions a reality this year.
Seasons Greetings, DigiSagers!
We’re feeling grateful for all of you—for the opportunities to know you and support your businesses.
In that spirit of gratitude, we’re paying it forward with a very special project.
WAFER Food Pantry came to us for help with a new website.
We surprised them…
…by telling them that the website would be free.
WAFER has an amazing mission. They feed hungry people in our community.
And while our cooking skills are just so-so, our design, marketing and website development skills are amazing. So we’re happy to put those talents to use to help nonprofit organizations in our community do what they do best. Last year it was the Greater La Crosse Area Diversity Council. This year it’s WAFER. Your support—choosing DigiSage as your marketing partner—makes this possible.
Stay tuned for the launch announcement.
Stay safe.
Do good.
Be happy.
Your friends,
Tim, Bob, Jason, and Randy
The team at DigiSage believes that making diversity, equity, and inclusion a priority is everyone’s responsibility, so we are pleased to support the efforts of the Greater La Crosse Area Diversity Council. We’ve donated a new, custom-designed website to help amplify their message and engage community members in their mission.
The new website features a warm, inviting design; is simple to navigate, making it quick and easy for visitors to access the various resources the GLADC makes available; finally, it promotes and recognizes GLADC members and makes it easy for supporters to donate or join the council.
Together, we will unite to create lasting change! If you’re not a member, please consider joining. Visit the site to learn more. https://www.glaxdiversitycouncil.com/
You’ve created a beautiful, easy-to-navigate design; crafted helpful, informative content; tested all the links; and now you’re ready to go live. Well, not quite yet. Make sure you don’t miss these three important steps to ensure your new website is positioned for success right from the get-go.
1. Set up permanent 301 redirects. If the new website is replacing an existing website, make sure you set up permanent 301 redirects from your old URLs to the new, corresponding URLs. 301 redirects tell Google and the other search engines, “Hey! Thispage is where this old page’s content now lives!” When you’re switching to a new website, this is one of the most important steps to ensure minimal disruption to your search engine rankings. 301 redirects pass most of the “SEO value” your old pages had accumulated to the new pages. They also redirect users to the new pages, so bookmarked links and old URLs in the search engine results pages (SERPS) will continue to function.
Note that 301 redirects are only needed when the URL structure is changing. For example, if your company’s Philosophy page URL used to be /company/philosophy but in the new site it’s going to be /about-us/philosophy, you would set up a 301 permanent redirect from /company/philosophy to /about-us/philosophy.
If certain pages’ content is not going to be brought over to the new website, don’t set up permanent 301 redirects for those pages. A common SEO myth is that you should 301 URLs for pages that have been removed to avoid 404 page not found errors. Don’t! 301 redirects are intended to tell Google and the other search engines when content has been moved. Setting up 301 permanent redirects to the home page for all pages that have been removed would be incorrect, since that content does not exist on the home page. Google even tells us, “404s are a perfectly normal part of the web; the Internet is always changing, new content is born, old content dies, and when it dies it (ideally) returns a 404 HTTP response code.” If you’ve deleted pages from your site (or aren’t bringing them over in a redesign) simply submit a URL removal request via Google Search Console to have Google remove those URLs from their index.
2. Customize your 404 page. In the event that you miss setting up a few permanent 301 redirects or forget to request removal of URLs that no longer exist in the website from Google’s index, you’ll want to make sure you have a useful 404 page set up. (A 404 page is the page visitors are directed to when the page they’re trying to access has been removed, or the link to your website they’re trying to follow is broken).
Consider including some friendly language explaining that the page no longer exists, rather than a generic “404” or “Not Found” headline. When it fits the company culture, the 404 page can be a great place for a little humor or just a something fun and lighthearted, like Amazon’s 404 page, which invites visitors to “meet the dogs of Amazon.” Include a few links to popular pages of the website (you can check your Google Analytics Behavior report to identify your site’s most popular pages) and either include a search box in the middle of the page, or direct the user to where it can be found (“Use the search box at the top of the page…”). It can also be a good idea to include your company’s contact information to make it easy for the visitor to reach you.
3. Add Google Analytics. Ideally the Google Analytics code should be added right before launch so it starts collecting data right away. If your old website was using Google Analytics, consider using the same UA code for continuity. Some webmasters may prefer to set up a new View for the new website, to have a fresh set of data. If you’re going to continue using the original views, make sure to update any goal URLs and audience definitions that may have changed. If it’s a completely new website, now is a great time to enable ecommerce tracking (if appropriate), define goals (such as Contact Us or Request a Quote form submissions), and create audiences for future remarketing campaigns.
If you’re going to be using tags from different programs (such as Google Analytics, Google Ads, the Facebook Pixel, HotJar, etc.), consider using Google Tag Manager to make installing and managing various tags easy.
Launching a new website is a big deal—typically, a lot of work goes into creating a professional website. Taking the time to complete these three steps before launch will help ensure your search engine rankings are only minimally impacted, that visitors continue to have a positive user experience, and that you’re collecting the data you need to continue to improve your website.
Internet hacking and data breaches have become a recurring theme in the news, but don’t fall into the trap of thinking that your site isn’t worth hacking, or that no one would take the time to try. The truth is, websites of all sizes and topics are the target of hacking attempts every single day. Today, hack attempts are coming not just from real live hackers, but from automated scripts that scour the web, sniffing out potential exploits and vulnerabilities everywhere they exist…from the multi-million dollar e-commerce site to the “I’m pretty sure my mom is the only person reading this” hobby blog. The goal of these exploits is no longer simply gaining access to financial information or credit card numbers. Now, hackers are after anything they can use to their advantage, and your website (no matter the size or scope) offers an abundance of such resources.
Server Resources
Storage
To a hacker, a vulnerable website could just as easily be seen as a gaudy neon sign advertising “Free Storage.” While some may just be attracted by the low price tag, others are trying to avoid storing illegal software and content on their own servers. As a website owner, footing a hacker’s bill is the least of your concern: you could be unwittingly hosting malware, and stolen data on your site. When storage is the purpose for the hack, the website itself typically remains unchanged, making this type of hack especially difficult to notice.
Bandwidth and Processor Resources
Another valuable commodity on the internet is bandwidth, and hackers are eager to commandeer a website for its share. Using stolen bandwidth, hackers are able to run their own programs on someone else’s server, thereby avoiding the cost. This bandwidth can also be resold for a profit. Processor hacking is especially prevalent after the explosion of cryptocurrency, as “miners” looking to cut costs find extra processing power by hacking vulnerable websites.
Online Reputation
Companies that operate online browsers and search engines want the internet to be safe to use, so they actively block malicious IP addresses (each website uses either its own unique IP address or a shared IP address with other sites on its server) from appearing in the search results. Unfortunately, this means malicious actors on the internet need to consistently find clean IP addresses to use. One of the most valuable assets your website has is its “reputation” on the internet. (When we say reputation, we mean the fact that its IP address hasn’t been flagged or reported for hosting malware). “Reputation” helps determine where a site ranks in the search engine result pages (SERPs) and can even impact visitors’ ability to access it (because Google and other search engines will sometimes remove URLs of sites infected with malware from its index).
By gaining access to your website, hackers can also gain access to your clean IP address – which they can use to execute phishing attacks. These attacks – used to steal passwords and financial information – are more successful with a clean IP address, which can trick failsafes such as Google Safe Browsing. Hackers may also want to send spam email from your clean IP address to get past spam filters, or use your site to attack another site (ensuring their own anonymity).
In the aftermath of these hacks, one of the most significant setbacks is the loss of your IP’s reputation, as your website has most likely been added to internet blacklists for malicious intent. This frustrating situation can be difficult to fix.
Traffic to Your Site
Redirects
Placing redirects on a site is a direct way a hacker can benefit from someone else’s web traffic. Redirecting users attempting to access your services to a dangerous site not only affects the credibility of your website, but your business in general. Hackers are refining this technique, and usually only instigate a redirect under certain conditions in order to avoid detection.
Drive-By Downloads
Another threat to a hacked website’s users is a “drive-by download,” or a download that happens without a user’s knowledge or understanding. These hacks are a common way to distribute malware, spyware, or viruses to your site’s visitors. Not only does this attack the reputation of your website and company, but it puts the privacy of your website’s visitors at risk.
Black Hat SEO
Search engine optimization (SEO) is a concern for anyone with a site to promote, and like most things in life, not everyone likes to play by the rules. “Black hat SEO” is a blanket term that refers to unethical or illegal techniques that violate a search engine’s terms of use. One black hat technique is for a hacker to gain access to a legitimate website and inject links to another website. Hackers offer this as a paid service. (Hint: don’t do it! The search engines impose strict penalties for “paid” links and devalue links from non-related websites).
Defacement
Blatant defacement of a site is one of the most brazen acts of hacking. While hackers usually want to remain undiscovered for as long as possible, sometimes hackers view defacing a site as a challenge. Hackers can also be engaging in “hacktivism,” supporting or rejecting a cause (often political) via someone else’s website. In layman’s terms, a hacker hijacks your website in order to display their own message or malicious content.
User Data
One of the most dangerous compromises a website can face is the breach of user data. If your site deals in e-commerce, this is especially serious as your visitors’ credit card information could be stolen and exploited. However, sites without e-commerce functionality are not immune from data breaches; other types of data such as personally identifiable information can be used by a hacker looking to make a profit. In addition, your visitors’ username and password combinations can be stolen and tried on other websites – when people use the same username and password for multiple sites, such as online banking – this can become a real problem.
The question is no longer why would anyone bother trying to hack my website, but rather, what can I do to ensure it’s not? Any site can be hacked, and every website has something valuable to protect. When you work hard to create something on the internet, it’s devastating to see it be taken advantage of. That’s why we at DigiSage take cyber security so seriously. Part of our approach to security includes taking daily offsite backups, running realtime antivirus scanning with alerts, using CloudLinux sandboxes, and consistently updating the sites we manage. Learn more about the online security measures we take to ensure the integrity of your website.
WordPress is open source software that can be used to develop and manage modern, engaging websites. 28% of the web uses WordPress including sites like NBC Sports, TED, CNN, Time, Dow Jones, UPS, Tech Crunch, Southern Bancorp, and Mint.edu.
Benefits of WordPress include:
Feature Rich: WordPress makes it easy to add new functionality with over 45,000 free or low-cost “plugins” that introduce features like sliders, advertising, forms, social media integration, contests, and more. Premium plugins that offer advanced features and additional support are also available. Plugins can be cost-effectively custom programmed to meet specific needs.
Publishing Tools: an intuitive interface and content editor make it easy for even non-technical users to add pages, edit content, and install new functionality. Page layouts are highly customizable. Built-in publishing tools allow administrators to create drafts and save them for publishing later, and even schedule new content to be published automatically later. Administrators can preview changes in a full-page preview before publishing. Additionally, administrators can roll back to earlier versions of each page, unlimited times. And, deleted pages are saved in the “trash” and can easily be recovered.
Media Management: WordPress websites automatically optimize images, and YouTube videos can be embedded by simply pasting the YouTube URL into the page.
Multi-Language Support: sites can be configured to allow users to choose their preferred language.
Accessibility Compliance: with proper theme programming and content management practices, WordPress websites can fully meet accessibility guidelines.
Speed & Performance: websites can be optimized for ideal speed and performance, providing an optimal user experience even on slower internet connections and mobile devices.
Beautiful Design Possibilities: any design can be programmed into a WordPress theme.
Mobile-Friendly: in addition to building a responsive (mobile friendly) theme, there are several plugins available to help ensure content like images, tables, and sliders remain mobile friendly.
Search Engine Optimization: WordPress is a search engine-friendly platform, with many tools available to help you implement additional search engine optimization (SEO) tactics.
Security: DigiSage uses multiple layers of security to protect our WordPress websites, including reverse proxy, a secure data center facility, many server security features, and security plugins on the WordPress website itself. In addition, we actively monitor our websites and install updates whenever needed.
Maintenance & Upgrades: the WordPress core and many plugins update automatically. When updates are available, they’re shown right on the WordPress dashboard, where they can be installed with the click of a button.
Support: WordPress is supported by a widespread community of developers, and there are many free resources and guides.
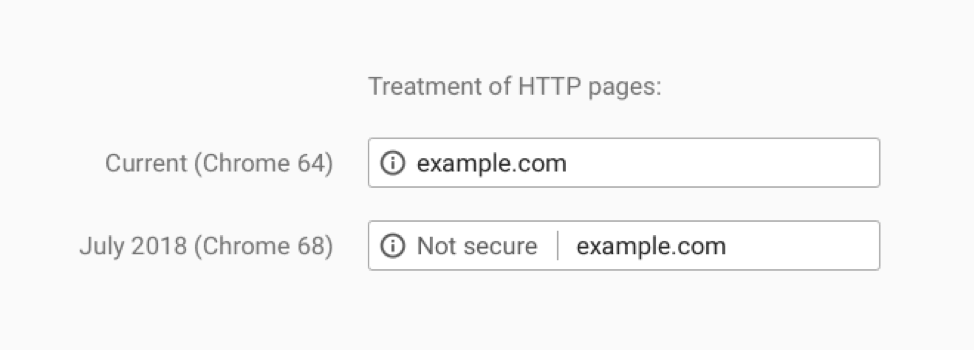
What is the Google Chrome “Not Secure” Warning?
Beginning in July 2018 with the release of Chrome 68, people who use Google Chrome as their web browser are being shown a “not secure” message in their browser bar when visiting websites that don’t use an SSL certificate (which encrypts the communication between your browser and the website). This message looks like:
Historically, websites that accepted and transmitted credit card payments were required by the Payment Card Industry (PCI) to use an SSL certificate, because if unencrypted credit card data was intercepted by hackers it could cause real problems. Other websites were not required to meet the same standard, though many sites that were collecting and transmitting other sensitive data, such as usernames and passwords, would still use SSL of their own accord. In 2014, to help encourage webmasters to develop a more secure web, Google started to use the presence of an SSL certificate as a ranking signal (ranking signals help determine how high up in the search results pages any given webpage shows up for particular search queries). Now, with the change to Google Chrome that shows sites without an SSL certificate as “not secure,” Google is further encouraging all sites to use SSL.
What is an SSL Certificate?
An SSL certificate (SSL stands for Secure Sockets Layer) is a digital certificate, issued by a certificate authority (CA), that encrypts information sent between your web browser and the website server, such as credit card information, usernames, and passwords (so if the data is intercepted, it is unintelligible and unusable without the proper decryption key). Some SSL certificates also confirm the identity of a website (that the website is actually the website the domain says it is, e.g., it’s not a spammy website posing as apple.com). When an SSL certificate is installed on a website’s server, instead of that website sending information through the standard HTTP protocol, it is sent through the HTTPS encrypted protocol.
Are there different types of SSL Certificates?
There are three types of SSL certificates available, and all provide encryption. Where they vary is in the level of “vetting” of the organization’s right to use the domain, and the amount of information about the organization that is collected and/or checked.
Domain Validated (DV) – domain validated certificates are the easiest to obtain, with the least amount of vetting. Certificate authorities will simply confirm the applicant controls the specific domain name they are applying for the certificate for.
Organization Validated (OV) – Before issuing an OV certificate, the certificate authority will confirm the applicant owns the domain they’ve applied for the certificate for, and requires the applicant to submit some additional information about its organization, including organization name, address, city, state, zip, and more.
Extended Validation (EV) – EV certificates are only issued once the company has been more vetted by the certificate authority, following strict guidelines that require the CA to check the organization’s legal, physical, and operational existence; that is has the right to use domain name the certificate is being requested for, and more. EV certificates, once installed, are indicated by the organization’s name appearing in green to the left of the domain in the browser window.
SSL certificates are also available as “single domain certificates,” “wildcard certificates,” and “multiple domain certificates.”
- Single domain certificates provide coverage for one domain (example.com) or subdomain (events.example.com).
- Wildcard SSL certificates provide coverage for multiple subdomains, such as example.com, shop.example.com, and events.example.com.
- Multiple Domain SSL certificates will cover multiple domains and subdomains.
The type of certificate you choose depends on the type of website you run – if it’s a basic blog or “brochure” site, you may not need anything more than a domain validated SSL certificate. If it’s an eCommerce site, a membership site, or a site where you’re asking your visitors to submit sensitive information, you may opt for an organization validated certificate, which provides added assurances for visitors that your site is “who” it says it is. Very few websites require extended validation certificates (and few companies or organizations are willing to pay for them).
Do I Need an SSL Certificate?
It’s a good idea for all sites today to use an SSL certificate, even if the website isn’t collecting sensitive data. Having an SSL certificate helps visitors feel more secure, and it is a small ranking factor in Google’s search algorithm which determines where sites rank in the search results.
How Much Does an SSL Certificate Cost?
SSL certificates range in price from several hundred dollars per year (for an EV cert) all the way down to free.
How Do SSL Certificates Work?
First, a certificate must be procured for the website and installed on the website’s server (where the website “lives”). You, your developer, or your hosting company will submit a certificate signing request (CSR) to a certificate authority like Let’s Encrypt, Comodo, DigiCert, GeoTrust, or others. The certificate signing request is generated on the server where the certificate will be installed and contains information that will be included in the certificate, such as the organization name, domain name, city/locality, state/county/region, and country. It also includes a “public key” which will be included in the certificate.
The certificate authority will then need to verify the applicant. Depending on which type of certificate you purchase, the validation process may be less, or more, involved:
- The validation process for “domain validated SSL certificates” is simple: the webmaster must either confirm they control the domain by replying to an email sent to the domain registrant email address, configure a DNS record for the website (which also proves they have control of the domain), or by uploading a file to the server.
- An organization-validated certificate requires the webmaster to both confirm ownership of the domain, and submit additional information about the company’s identity, including organization name, city, state, and country.
- An extended validation or EV certificate requires additional verification – the certificate authority will verify that the business is a real legal entity in addition to requiring business information be submitted that provides proof of domain ownership.
Once the certificate authority has completed the validation process, it issues the certificate to the applicant, who then needs to install it on the website’s server.
Then, when a visitor accesses a website using their browser (such as Google Chrome), the browser sends a message to the website server, basically asking the server to identify itself. The website server responds with the information that the browser needs, including a copy of its SSL certificate.
Next, the browser will check whether that SSL certificate is from a trusted Certificate Authority, and that it’s not expired. If it passes, the web browser generates a “key,” which it encrypts and sends to the website server; the website server decrypts the key using its own private key, and sends back a “digitally signed acknowledgment” which completes the “handshake” between the browser and the server – both now agree that a secure connection has been established and that information the browser sends to the server can be encrypted, then decrypted by the server.
How Do I Get and Install an SSL Certificate?
Generally, you’ll want to work with a website developer and/or hosting provider to configure your site for SSL and to procure and install the SSL certificate itself. For most companies, DigiSage recommends using the free SSL certificate provided by Let’s Encrypt (an open certificate authority managed by a nonprofit governed by industry leaders). Anyone with a domain name can use Let’s Encrypt to get an SSL certificate for free; in addition, Let’s Encrypt certificates can be set up to renew automatically. Let’s Encrypt issues both single domain certificates and wildcard certificates.
Issues to Watch For
Expired Certificates
Unless you’re using a certificate from a certificate authority like Let’s Encrypt, which can be automatically renewed every 90 days, you may be required to take manual steps to renew your SSL certificate every one to three years. Notifications to renew will be sent to the email address the SSL certificate was registered with, so make sure that email is monitored and appropriate steps are taken to review the certificate before it expires. Failing to do so can result in the “not secure” message being displayed to your website visitors.
Mixed Security Elements from Embedded Content
If you are embedding content in your website from a third-party source (the content “lives” on another website but you are displaying it in yours – such as a video, a calculator, etc.) you must ensure that content is being served over HTTPS as well. If the site you are embedding the content from doesn’t use an SSL certificate, browsers may warn users that your page is not fully secure. If the other website is using an SSL certificate but your code is requesting the content over HTTP, all you need to do to fix the error is change your code to request the URL over HTTPS rather than HTTP: https://example.com rather than http://example.com.
If the other website is not using SSL, you can ask them to add SSL to their website, then once they do, update the code on your website to request the URL over HTTPS rather than HTTP.
If the other website is unwilling to add an SSL certificate to their website, you may consider removing their embedded content from your site to avoid the mixed content warning, which may confuse or scare your website visitors.
In addition, when adding an SSL certificate for the first time, fonts, images, and other embedded media URLs need to be updated from HTTP to HTTPS.
Certificate Mismatch Error
Certificate mismatch errors occur when the SSL certificate is issued for the wrong domain – often https://www.example.com, when the site is actually configured to show content on https://example.com (no www). When registering the certificate, webmasters should be careful to enter the exact domain the site uses. (If the site returns content on both www and non-www versions of the domain, set up a canonical redirect from one to the other first, to fix this problem and also to avoid duplicate content penalties in Google).
Google Search Ranking Fluctuations
According to Google, when migrating from HTTP to HTTPS, “as with all migrations, you may experience some ranking fluctuation during a migration.” Taking proper steps to manage the migration will minimize any impact, and ultimately, moving to HTTPS is a smart idea. Be sure to verify the HTTPS version of the site in Google Search Console (in fact, you should verify all four versions as properties in Search Console: http://www.example.com, https://www.example.com, http://example.com, and https://example.com.
Reminder: “Secure” Doesn’t necessary Mean “Safe”
Just because a website has an SSL certificate installed, doesn’t necessarily mean the website is safe – it just means that information you submit is being encrypted as it’s sent to the server. If the website or server isn’t being properly maintained, the website could still be vulnerable to hacking, which could result in spam links being injected into the website, driving visitors to malicious or deceptive sites; or malware being added to the site, which could also impact its visitors. Adding an SSL certificate to your website is just one component of maintaining a secure, reliable website.
Get Started
DigiSage can request a certificate on your behalf, install it, and keep it up-to-date automatically. Contact us for an estimate (though the certificate itself may be free, there are support costs involved in setting up the certificate and configuring the website to use it).
According to Google, the number of hacked sites increased by approximately 32 percent in 2016 compared to 2015, and each week, Google blacklists around 20,000 websites for malware and around 50,000 for phishing. Cyber security is a real (and growing) issue, which is why DigiSage takes the security of the websites we develop so seriously.
Common Types of Website Compromises
Websites can be hacked in a variety of ways and for a variety of reasons. Common hacks include:
- Content Spam: most common. Spammers inject content into a legitimate website to drive traffic to a malicious or deceptive site.
- Malware: software with the intent of doing harm to data, devices, or people.
- Credit Card Skimming: affects e-commerce platforms. It can also be considered as one of the most dangerous compromises for consumers as credit card data is stolen.
- Botnets: A botnet is a network of computers infected with malicious software and remotely commanded and controlled by cybercriminals called botmasters. Botnets steal your resources in order to do malicious things like crack passwords or crack other sites.
Why Should You Care?
Business owners and webmasters should be very concerned with the security of their websites, for a number of reasons:
- Google’s algorithm penalizes hacked sites in the search engine results pages (SERPS)
- Users may not be able to access your site
- You and your users’ data may be compromised
- Your brand’s reputation will be affected
- Fixing a hacked site can be difficult (and expensive)!
DigiSage’s Website Development Platform of Choice: WordPress
We develop the majority of our websites on the open source platform WordPress (wordpress.org). WordPress is a widely adopted and highly trusted website development platform: currently, 29% of the web uses WordPress—that’s over 1 in 4 websites online today! Security in WordPress is taken very seriously, but as with any other system there are potential security issues that may arise if some basic security precautions aren’t taken. DigiSage understands the importance of keeping the sites we develop secure, which is why we utilize multiple layers of security to ensure our sites remain safe.
Data Center Security and Redundancy
- Third-party SOC3 report for Liquid Web is available.
- State-of-the-art private data center facilities in Lansing, MI and Phoenix, AZ
- 24/7/365 staffed facilities
- Redundant network connections and hardware
- Redundant power feeds & HVAC
- Battery & diesel backup
- Building security including secure entrance with Access Card System
- Remote monitoring by 3rd Party Security Company
- Entrances Secured by Mantraps with Interlocking Doors
- SSAE-16 & HIPAA Compliant, Safe Harbor Certified
Server Level Security
- Apache’s Mod_Security Web Application Firewall
- Intrusion Detection coupled with firewalling
- Antivirus
- Regular Data Backups: daily backups on-server and off-site
- Enforced TLS connections
WordPress Platform Security
Since its inception in 2003, WordPress has undergone continual hardening so its core software can address and mitigate common security threats, including the Top 10 list identified by The Open Web Application Security Project (OWASP) as common security vulnerabilities. Learn more about the WordPress core software development and its related security processes, as well as an examination of the inherent security built directly into the software, here.
What else makes the WordPress platform highly secure? WordPress is the most widely-used CMS software in the world and it powers more than 29% of the top 10 million websites, giving it an estimated 58% market share of all sites using a CMS. Additionally, there are hundreds of thousands of WordPress developers. Due to the large number of users, issues with open source platforms like WordPress are often discovered, publicized, and addressed faster.
Individual WordPress Website Security
- Use of custom theme reduces attack surface: rather than using a commercial theme which may stop being supported or come with extra features (i.e. multiple sliders, contact forms, etc.) that are unused, we produce custom themes which include only the features required for the specific website. Reducing the amount of unused code makes the attack surface smaller and the site more maintainable.
- Anti-brute force: by using software which monitors login attempts we are able to throttle repeated attempts to reduce the amount of password guesses per second, as well as block an IP number when too many failed attempts have been made.
- Web Application Firewall (rules, malware signatures, malicious IP lists): by using a web application firewall we are able to apply rule sets to incoming requests and block them based on known bad request signatures, known bad IP numbers, and known attack patterns.
- Access controls:
- Secure password rules enforced: by enforcing more stringent password rules we can stop users from setting an easily-guessed password and avoid compromise by password guesses.
- Appropriate Access Controls: by providing a unique username and password per website administrator we are able to ensure access is revocable at any time.
- Logging of user actions: by logging actions taken by users we are able to reconstruct changes to content, installation and upgrade of plugins, and login history, etc.
- Multi-Factor Authentication: multi-factor authentication adds a second factor to user login which enhances login security by requiring the user to provide something they know (their password) as well as something they have (their cell phone) to authenticate.
- Regular Data Backups: daily backups using VaultPress
- Continuous monitoring for suspicious activity and anomalies using WordFence (free or premium versions available) & Vaultpress
Active Monitoring and Maintenance
Security patches for WordPress are widely published and readily available; many updates are automatically installed, while DigiSage actively and quickly plugs exploitable vulnerabilities by applying appropriate patches for items that don’t auto-update.
Core Updates: Starting with version 3.7, WordPress introduced automated background updates for all minor releases, such as 3.7.1 and 3.7.2. The WordPress Security Team can identify, fix, and push out automated security enhancements for WordPress without the site owner needing to do anything on their end, and the security update will install automatically.
Plugins: We only use vetted, supported, well-established, and widely-used plugins. Additionally, when a plugin vulnerability is discovered by the WordPress Security Team, they contact the plugin author and work together to fix and release a secure version of the plugin. If there is a lack of response from the plugin author or if the vulnerability is severe, the plugin/theme is pulled from the public directory, and in some cases, fixed and updated directly by the Security Team.
On our WordPress maintenance plan, we utilize special software that checks for updates multiple times per day—we monitor this daily; we also monitor the WordPress announcement list and the WordPress security lists and install updates whenever needed.
Search engine optimization is the process of configuring a website in such a way as to encourage the search engines to rank it well in the search results for particular keywords and phrases. To understand how search engine optimization (SEO) works, it can be helpful to understand how the search engines work. Here’s a brief overview.
How the Search Engines Work
- Google and other search engines like Bing are businesses that derive much of their revenue from paid advertising.
- Advertisers choose to advertise on the search engines because the search engines draw many users.
- These users choose to utilize particular search engines (primarily Google) because the search engines help them quickly find the information and resources they’re looking for.
- The search engines do this by returning what they identify as the best possible websites to meet the intent of each individual search that is conducted.
- To determine what websites will best meet searchers intentions or answers searches questions, the search engines rely on algorithms. The search engines “crawl” or “spider” websites to gather information about them. Once a web page has been crawled by the search engines, it may be added the search engine’s “index” of pages which can be returned in the search results in response to a user’s search query.
Common Search Engine Ranking Factors
The search engine’s algorithms take into account a variety of characteristics, including:
Content: does the website have fresh, relevant, unique content that will answer the searcher’s question? Is the content shallow, or substantive?
Age: has the website been around for a fair amount of time?
Reputation: are other well-ranked and related websites linking to the site in question? Inbound links represent a “vote of confidence” from real people (webmasters). In other words, those webmasters must have thought this site’s content was important or useful, so they added a link to it from their own website.
Social: are people (and especially influential people, with lots of connections) sharing links to the website on social media?
Speed: does the website load quickly? (Websites that load quickly will provide a better user experience than slow websites, and the search engines want users to have a good experience)
Security: is the website safe, or is it infected with malware?
Mobile friendly: is the website programmed to function well on mobile devices?
Structure: is the site programmed in such a way as to allow search engines to easily ‘crawl’ the site, to discover each page?
HTML: has the site been optimized to help the search engines understand the main topic of each page?
The search engines’ algorithms also take into account the personal search history of the individual user. In an effort to best match search results to that individual, the search engines will also look at:
History: has the website been visited by this user in the past? This may indicate the user has a preference for this website.
Geography: what country and city is the user located in?
A common misconception about search engine optimization is that it’s something that is done to the site as a whole–which is only partially true. Some SEO tactics, like ensuring the website is mobile friendly, is not infected with malware, and is programmed in a way that allows the search engines to discover all of the content are tactics that improve the site as a whole. However, we must take care to optimize individual pages of the site as well, for particular topics, since individual pages are what the search engines return in the search results in response to individual searches. For example, if a user types the search phrase ‘running shoes’ into the search engine, the search engine is more likely to return a web page devoted exclusively to ‘running shoes’ rather than a web page that is more generically focused on ‘shoes.’ An important part of search engine optimization is understanding and anticipating what people will be searching for, how people will be searching for it, and then tailoring individual web pages to meet those requests. This is where keyword research and building focused, content-rich pages becomes important.
To make matters more complex, the algorithms the search engines use are evolving, as the ways people search change, as the information people want (and how they want to receive it) change, and as technology changes. The importance of various factors within the algorithms change as well, so websites need to adapt and change with them. That being said–while the technical execution may change, in general, providing a great user experience and high quality, relevant information remains the best way to rank well in the search engines.